Home Page › Keeps your rdp / cloud desktop secure
Keeps Your RDP / Cloud Desktop Secure
Why to secure your RDP?
Remote Desktop Protocol (RDP), the Microsoft Windows component that makes it easy for your employees to connect to work or home computers while they are away, is used by millions. Because RDP is so widely used, it is a common target for man-in-the-middle cyberattacks.
While RDP can be a very effective productivity tool — it lets you connect to a remote desktop — failing to configure it correctly will allow attackers to hack into your machines.
Cybercriminals scan the internet to look for systems with open RDP ports and employ brute force tools to login to a machine. Once they gain access, they disable any pre-installed security solution like antivirus and then launch ransomware.
Ransomware like SamSam, CryptON and CrySIS have all been spread through RDP attacks. So, what can we do to prevent RDP attacks?
Ransomware attacks are increasingly using the Remote Desktop Protocol as the initial entry vector, taking advantage of the fact that many enterprises struggle to balance the risks of exposing RDP and the advantages of being able to access machines in multiple locations.
While there are many alternatives, Microsoft’s Remote Desktop is a perfectly viable option for accessing other computers, but it has to be properly secured. After recommended security measures are in place, Remote Desktop is a powerful tool for geeks to use and lets you avoid installing third party apps for this type of functionality.
Your anti-virus software won’t necessarily protect you
Ransomware is constantly being written and tweaked by its developers, and so its signatures are often not caught by typical anti-virus programs. In fact, as many as 75 percent of companies that fall victim to ransomware were running up-to-date endpoint protection on the infected machines.
How Do Hackers Breach a Company via RDP?
Attackers generally breach RDP by:
- Port scanning and brute-forcing RDP credentials with sites like Shodan.
- Purchasing leaked credentials on sites like XDedic.
- Phishing an employee of the company to gain access and control of their machine. Then brute-forcing RDP access from inside the network via the compromised machine.
There are tens of thousands of corporate RDP credentials available for sale for as little as $3 on dark web marketplaces. The wide availability of hacked RDP credentials is low-hanging fruit for cyber criminals looking to launch ransomware attacks. If ransomware like Dharma or SamSam strikes, it’s likely not the initial breach. The first breach likely led to the compromise of RDP access credentials that were subsequently sold to the ransomware hacker.
What Happens After a Hacker Gains Access via RDP?
Once in the network, the hacker will use tools like mimikatz to harvest administrative credentials and elevate access privileges across the domain. The administrative privileges can be used to disable anti-virus, two-factor authentication, or wipe/encrypt backups.
The hacker will typically take network notes so that they understand the topography of the network that they are about to cripple with ransomware. These notes help the hacker understand how the company will respond, and how they can most effectively curtail that response and increase the odds receiving a ransom payment.
The hacker then waits for an optimal time before pushing the ransomware executables into the most valuable portions of your network. Nights, weekends or holidays are common, as are important periods of time for your business. The executables encrypt PCs, servers, databases, applications and any backups that the hackers discovered. Once complete, the ransomware executables generally delete themselves and leave nothing behind but encrypted files and ransom notes.
How secure is Windows Remote Desktop?
Remote Desktop sessions operate over an encrypted channel, preventing anyone from viewing your session by listening on the network. While Remote Desktop is more secure than remote administration tools such as VNC that do not encrypt the entire session, any time Administrator access to a system is granted remotely there are risks. The following tips will help to secure Remote Desktop access to both desktops and servers that you support.
What Are Best Practices for Securing RDP from Ransomware?
Use strong passwords
Strong passwords on any accounts with access to Remote Desktop should be considered a required step before enabling Remote Desktop. Passwords must be at least eight characters long and include uppercase and lowercase letters, numbers, and characters. They should not resemble any previously used passwords.
Set an account lockout policy
By setting your computer to lock an account for a set number of incorrect guesses, you will help prevent hackers from using automated password guessing tools from gaining access to your system (this is known as a “brute-force” attack). To set an account lockout policy:
- Go to Start–>Programs–> Administrative Tools–> Local Security Policy
- Under Account Policies–> Account Lockout Policies, set values for all three options. Three invalid attempts with 3-minute lockout durations are reasonable choices.
Use Brute Force Protetcion
One common tactic is RDP brute-forcing, where attackers automate many login attempts using common credentials, hoping one hits. A new module in Trickbot specifically tries to brute-force RDP accounts, as such brute force protection is highly recommended. We strongly recommend RDP Guard for that –
We offer following volume discount pricing on RDP Guard
| Unit price (USD) | ||||
| First 1 | Next 2 – 6 | Next 7 – 20 | Next 21 – 50 | Next 51 – .. |
| $60 | $48 | $43 | $36 | $28 |
Update your software
One advantage of using Remote Desktop rather than 3rd party remote admin tools is that components are updated automatically with the latest security fixes in the standard Microsoft patch cycle. Make sure you are running the latest versions of both the client and server software by enabling and auditing automatic Microsoft Updates. If you are using Remote Desktop clients on other platforms, make sure they are still supported and that you have the latest versions. Older versions may not support high encryption and may have other security flaws.
Enable Network Level Authentication
Windows 10, Windows Server 2012 R2/2016/2019 also provide Network Level Authentication (NLA) by default. It is best to leave this in place, as NLA provides an extra level of authentication before a connection is established. You should only configure Remote Desktop servers to allow connections without NLA if you use Remote Desktop clients on other platforms that don’t support it.
Use Two-factor authentication
Departments should consider using a two-factor authentication approach. This topic is beyond the scope of this article, but there are many options available. One of the best free options is One time password authentication for Windows remote desktop environments : https://github.com/sbeh/RDP-OTP
Other Paid options include DUO or smartcards. This approach utilizes the Remote Desktop host itself, in conjunction with YubiKey and RSA as examples.
Use a Virtual Private Network
When you use a Virtual Private Network (VPN) connection, you add an extra layer of RDP security to your system. The VPN ensures that before a connection can be made to your server, a connection must be made to the secure private network, which is encrypted and hosted outside of your server. When your computer is connected to the VPN, it is assigned a private IP address used to open the remote desktop connection to the server. That means attempts from outside IP addresses to connect will be rejected. We recommend using zerotier.com – Free for most of the users
Use a Remote Desktop Gateway
An RDP gateway (in conjunction with a VPN) enhances control by removing all remote user access to your system and replacing it with a point-to-point remote desktop connection. Users go to a login page, enter credentials, and get connected to the network through a firewall. Microsoft has built RDP gateway functionality into its Windows servers, which is where the current risk for legacy computers is found.
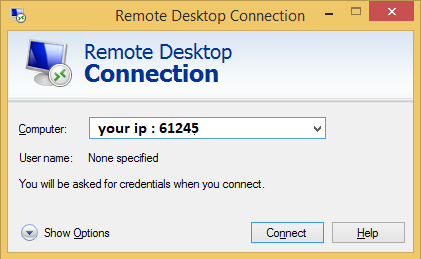
Change Default RDP Port
By default, Remote Desktop listens on port 3389. Pick a five digit number less than 65535 that you’d like to use for your custom Remote Desktop port number. With that number in mind, open up the Registry Editor by typing “regedit” into a Run prompt or the Start menu.

When the Registry Editor opens up, expand HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Control > Terminal Server > WinStations > RDP-Tcp > then double-click on “PortNumber” in the window on the right.

With the PortNumber registry key open, select “Decimal” on the right side of the window and then type your five digit number under “Value data” on the left.

Click OK and then close the Registry Editor.
Since we’ve changed the default port that Remote Desktop uses, we’ll need to configure Windows Firewall to accept incoming connections on that port. Go to the Start screen, search for “Windows Firewall” and click on it.

When Windows Firewall opens, click “Advanced Settings” on the left side of the window. Then right-click on “Inbound Rules” and choose “New Rule.”

The “New Inbound Rule Wizard” will pop up, select Port and click next. On the next screen, make sure TCP is selected and then enter the port number you chose earlier, and then click next. Click next two more times because the default values on the next couple pages will be fine. On the last page, select a name for this new rule, such as “Custom RDP port,” and then click finish.
Your computer should now be accessible on your local network, just specify either the IP address of the machine or the name of it, followed by a colon and the port number in both cases, like so: